Overview
Unity Technologies has disclosed a high-severity vulnerability (CVE-2025-59489) affecting all Editor and Runtime versions since 2017.1. The flaw allows arbitrary code execution through unsafe argument handling and untrusted library loading paths across Windows, macOS, Linux, and Android builds. The security score is 8.4 / 10 (High), making this one of Unity’s most serious engine issues in years.
While no exploits have been observed in the wild, the scale of exposure prompted immediate delisting of several titles on Steam and Google Play until developers issue fixed builds.
Who Is Affected
- All Unity projects built on Unity 2017.1 through 2022 LTS and 6000.x early releases.
- Games distributed on Windows, Android, macOS, and Linux.
- Projects using custom plugin loading or dynamic content ingestion.
Consoles and cloud builds are less affected due to sandboxing, but local desktop and mobile versions remain vulnerable if unpatched.
What Developers Must Do Immediately
- Update the Unity Editor and Runtime Download patched versions from Unity’s official advisory. The patch resolves unsafe search path behaviors and argument injection vectors.
- Rebuild and Redeploy All Versions Re-open your project in the updated Editor, rebuild, and re-publish across all storefronts. This ensures bundled runtime binaries are replaced with secure ones.
- Use Unity’s Binary Patch Tool (if rebuild isn’t feasible) Unity has released a binary patch utility that updates
UnityPlayer.dlland runtime libraries in existing builds. - Audit Plugin & File Load Logic Review all dynamic
DllImportorAssembly.Loadstatements and restrict file access to trusted directories. - Communicate Updates to Players Publish patch notes and prompt users to download fixed builds immediately.
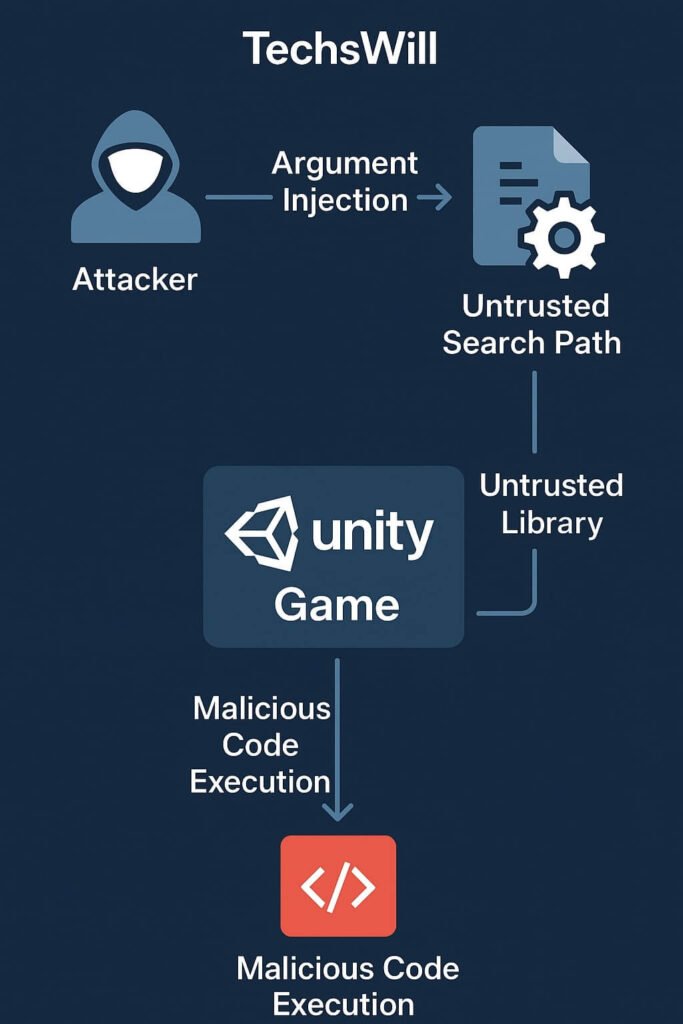
How the Vulnerability Works
The issue stems from Unity’s command-line parsing mechanism and dynamic library search behavior. Attackers could craft payloads or local files that Unity inadvertently loads at runtime, executing malicious code under the same privileges as the game.
Technical Summary
- Vector: Untrusted search path / argument injection.
- Impact: Arbitrary code execution, sandbox escape, privilege escalation.
- Exploit Complexity: Moderate — requires local or chained access.
Verification & Hardening Steps
After patching, confirm the following in your build environment:
- Validate your
UnityPlayer.dllchecksum against the patched hash list. - Use Code Signing and App Sandbox on macOS builds.
- Restrict library search paths via environment variable sanitization.
- Re-enable runtime integrity checks before shipping.

Broader Takeaways — Secure Engine Workflows
This event reminds developers that even production-ready engines can expose security surfaces. Going forward:
- Automate Unity patch scanning in CI/CD pipelines.
- Isolate AI model loading or plugin ingestion behind sandbox wrappers.
- Audit save systems, network IO, and content downloads for external code references.
- Review permissions and clean unused assets or DLLs regularly.
Security isn’t a one-time patch — it’s a continuous pipeline discipline.


